
Best Portable Bluetooth Speakers In India Under 10 000
The LINK-KEY being the pairing key that is used to authenticate devices with each other. This would also require passive sniffing then using BTCrack to break it. Try to utilize your bluetooth with the programs that come with Kali and if you’re able to use it look at the resources that u/mylifeinbinary010101 suggested.

The best Bluetooth speakers for iPhone and iPad Cult of Mac
Strangers connecting to your Bluetooth speakers? Input jack getting overridden by unknown Bluetooth connections? I show how I stopped it on Klipsch ProMedi.

Nest issues software update for Bluetooth hijacking bug
Thank you for watching I hope you enjoyed. Please kindly subcribe to the Channel so that you will be notified on our next episode.Download the song here : ht.

Speakers With Everything Except the Sticker Shock Wireless speakers
A: Bluetooth Speaker Hijacking is a type of attack where an attacker takes control of a Bluetooth speaker to gain access to the devices services and features. This type of attack can be used to intercept audio or data, install malicious software, or gain access to the devices resources.

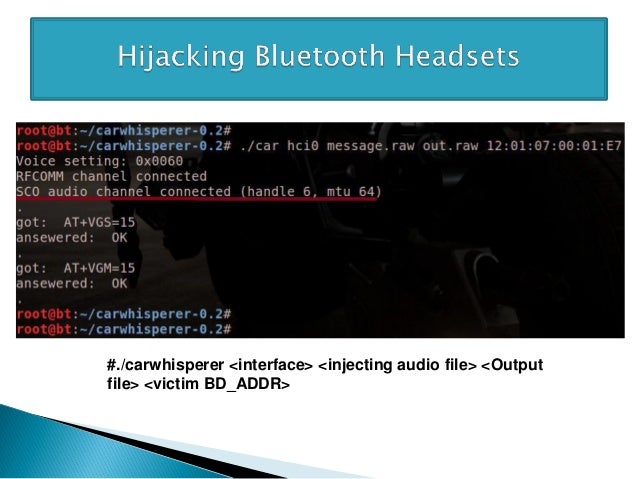
Hijacking bluetooth headsets
You will be able to hijack a Bluetooth speaker by first escalating the KNOB attack. With KNOB opening the door, escalate the attack a step further by leveraging your access to the decrypted link in a controlled environment and hijacking the Bluetooth session. Set Up A Man In The Middle Attack

Hackers can remotely hijack thousands of Sonos and Bose speakers to
The Bluetooth spectrum is split into 79 1MHz-wide bands. Every Bluetooth device is capable of hopping to a different band 1,600 times per second. This makes the connection more resilient against some re-pairing attacks Fortunately, Bluetooth has robust systems in place to prevent re-pairing attacks.

Audio Hijack for Mac Download Free 2022 Latest Version
Bluejacking: Using one Bluetooth-enabled device to hijack another and send phishing messages; Bluesnarfing: Extracting information from a device through a Bluetooth connection;. A Bluetooth speaker, for example, communicates with the app on your mobile phone by broadcasting a universally unique identifier (UUID).
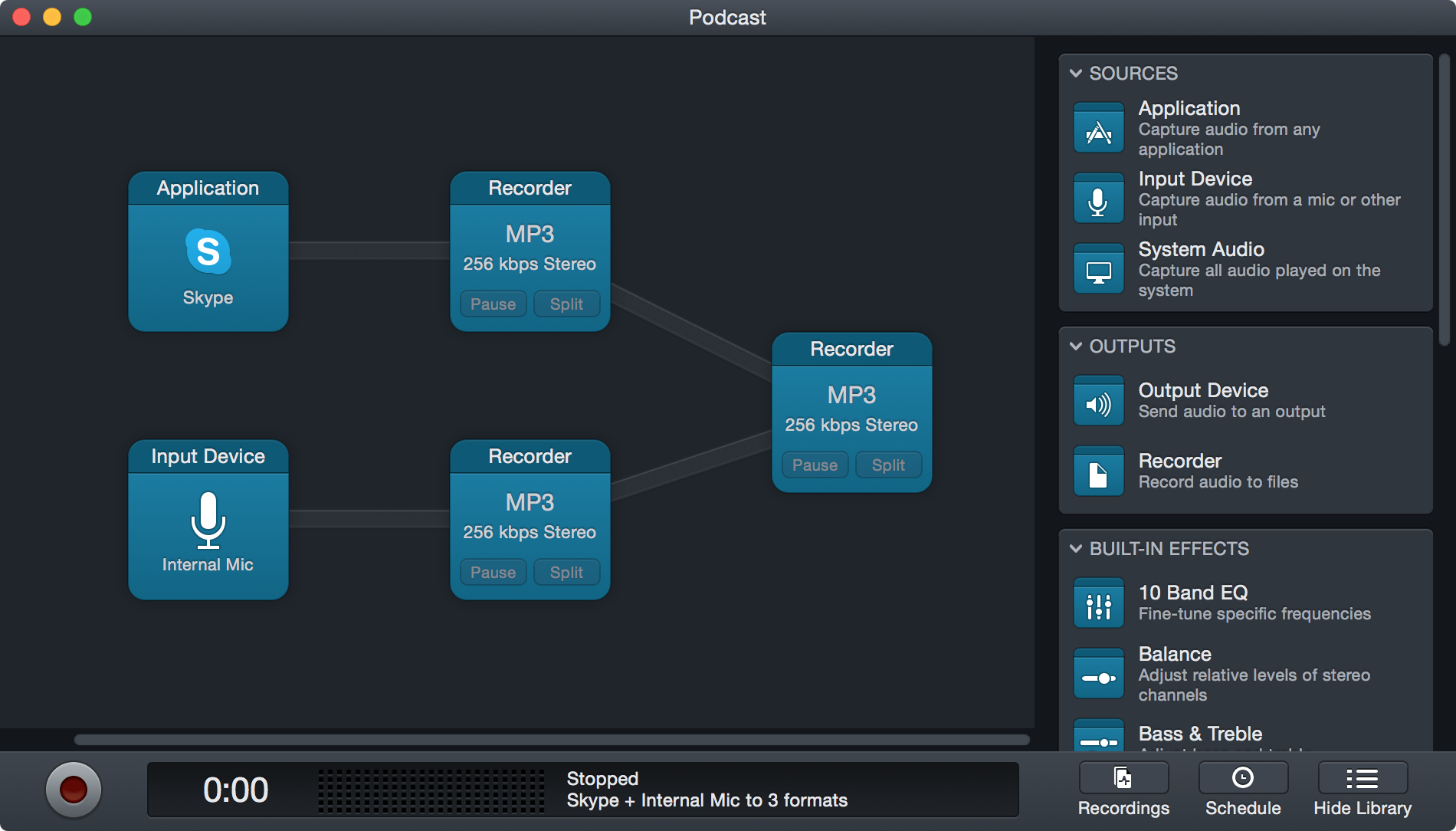
Learn to Record Anything with Take Control of Audio Hijack TidBITS
To do this: Check to see if the Bluetooth speaker is switched OFF. Go to Settings, then click Bluetooth on the device you want to connect (for example, your phone) and look for your speaker in the list of Bluetooth devices. To connect, turn ON the Bluetooth speaker. After pressing the connect button, turn the speaker ON while your device tries.
Hijacking bluetooth headsets
Read on to learn all the ways to override a Bluetooth speaker. How To Hijack Or Hack A Bluetooth Speaker. People can use various methods to hack a Bluetooth speaker. These include: Being the first person to pair with the Bluetooth speaker; Finding vulnerabilities in a Bluetooth speaker; Executing a KNOB (Key Negotiation of Bluetooth) Attack

Researcher finds huge security flaws in Bluetooth locks AIVAnet
Swipe down from the top of the screen to bring down the Notification menu, then tap the “Bluetooth” icon in the resulting drop-down. If the “Bluetooth” icon is highlighted or blue, it’s already on. You may have to turn on Bluetooth for the other phone as well. 4 Connect to the phone you want to hack.
Hijacking bluetooth headsets
The first step in hijacking a Bluetooth speaker is to identify susceptible devices. This involves scanning the area for any Bluetooth enabled devices that are not properly secured. To do this, attackers can use specialized tools such as Bluetooth scanners or wireless sniffers. These tools can be used to detect any vulnerable devices in the.
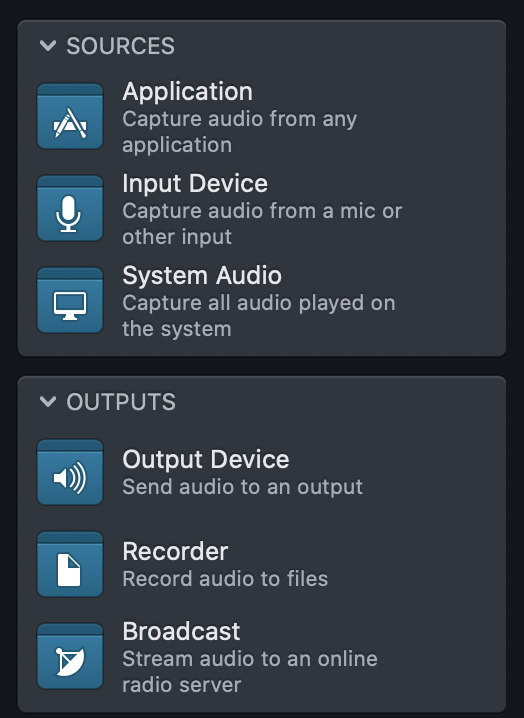
Interesting Audio Hijack Sessions Podfeet Podcasts
NOTE: This video was made for educational purposes only. All activities shown in this video are demonstrated for educational and informative learning.I final.

A Sonic Cyberattack Could Hijack A Device s Speakers Tech
A lot of speakers are pairable when they’re not streaming music but still on. Get close, look for Bluetooth devices and see if you can just pair with them. The thing about hijacking is that once someone is connected, you just take over the thing. I think this is op point.

Session Hijack and Session Hijacking Basics Audio Osx Mac os
How to Hijack or Hack a Bluetooth Speaker 1. Pair with It Before Anyone Else This is the simplest way to take over a Bluetooth speaker. If you are the first person to pair with the speaker, you will be able to control it. Most Bluetooth speakers come with a default PIN. However, some don’t.

Hijack Development Pack
Step 2: Route the audio output for each Mac app to different speakers. 1) Go to Audio Hijack’s website and click Free Download. Double-click the zip file to open it if it hasn’t already. Next, launch the Audio Hijack app on your Mac. You may have to attend to some alerts in System Settings and restart your Mac a couple of times.

Hackers Could Play Deafening Noises On Your Speaker By Hijacking It
Way 1 – Be the First One to Pair Up The easiest way to connect to your speaker is by being the first one to pair up. This lets you have full control over the device. Most of the speakers have a built-in default PIN. But if a speaker lacks this default PIN, it is easy to hijack it. Way 2 – Use the Efficient KNOB Attack